OWASP SwitchBlade (formerly known as HTTP Post/DoS Tool) is an open source program that allows you to perform Denial of Service attacks on web applications. If you are a web app developer, then it is a great tool for you, you can use it to test the stability of your web applications against HTTP Post, Slowloris, and SSL renegotiation attacks.
Let's talk about the attacks...
- HTTP POST Attack
When an HTTP client (ex: web browser) communicates with a server, it sends an HTTP request: GET request or a POST request.GET requests are used to retrieve standard, static contents (ex: images), and POST requests are used to access dynamically generated resources.
And you probably know that the DoS attacks are most effective when it forces the server or the application to allocate the maximum resources possible in response to each single request, and the POST requests are capable of doing that - it allows you to include parameters that can trigger complex server-side processing. That is the main reason why attackers choose HTTP POST attacks instead of HTTP GET attacks.
HTTP GET based DoS attacks are good only if you have a botnet or a large network.
Other limitations of HTTP GET attacks:
- Does not work on IIS web servers or web servers with timeout limits for HTTP headers.
- Easily defensible using popular load balancers, such as F5 and Cisco, reverse proxies and certain Apache modules, such as mod_antiloris.
- Anti-DDOS systems may use delayed binding or TCP Splicing to defend against HTTP GET attacks.
The next one is...
- Slowloris Attack (Slow headers):
In this type of attack, the attacker sends partial HTTP requests (not a complete set of request headers) that continuously and rapidly grow, slowly update, and never close. The attack continues until all available sockets are taken up by these requests and the Web server becomes inaccessible.
Note: SwitchBlade allows only 40000 connections. So you might need a larger network for a successful Slowloris attack.
The last attack is...
In this type of attack, the attacker sends many renegotiation requests (SSL handshake) to the server - overwhelming the server to a point where it can't handle it.
It also has "40000 connections" limit. So, for a successful attack, you might need the support of a larger network or a botnet.
- SSL Renegotiation Attack:
In this type of attack, the attacker sends many renegotiation requests (SSL handshake) to the server - overwhelming the server to a point where it can't handle it.It also has "40000 connections" limit. So, for a successful attack, you might need the support of a larger network or a botnet.
How To Use OWASP SwitchBlade
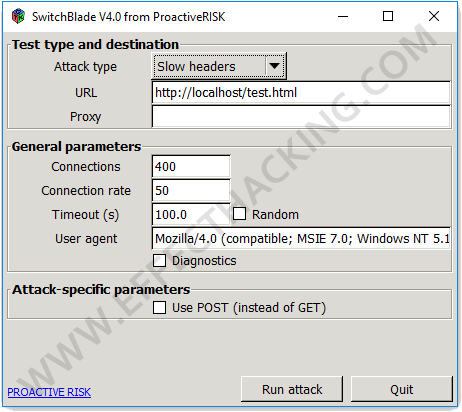
First, download OWASP SwitchBlade (download links are at the end of this article). Then run the "gui.exe", you will see a window as shown below.
Now, select the attack type, enter the target URL, and then configure "General parameters" and "Attack specific parameters". Then click on the "Run attack" button. That's it.
That's all. I hope you liked it. If you did, please share...
You might also like:
OWASP SwitchBlade - An Open-Source Denial of Service Attack Tool
 Reviewed by AC10 Tech
on
Monday, March 15, 2021
Rating:
Reviewed by AC10 Tech
on
Monday, March 15, 2021
Rating:
 Reviewed by AC10 Tech
on
Monday, March 15, 2021
Rating:
Reviewed by AC10 Tech
on
Monday, March 15, 2021
Rating:




No comments: